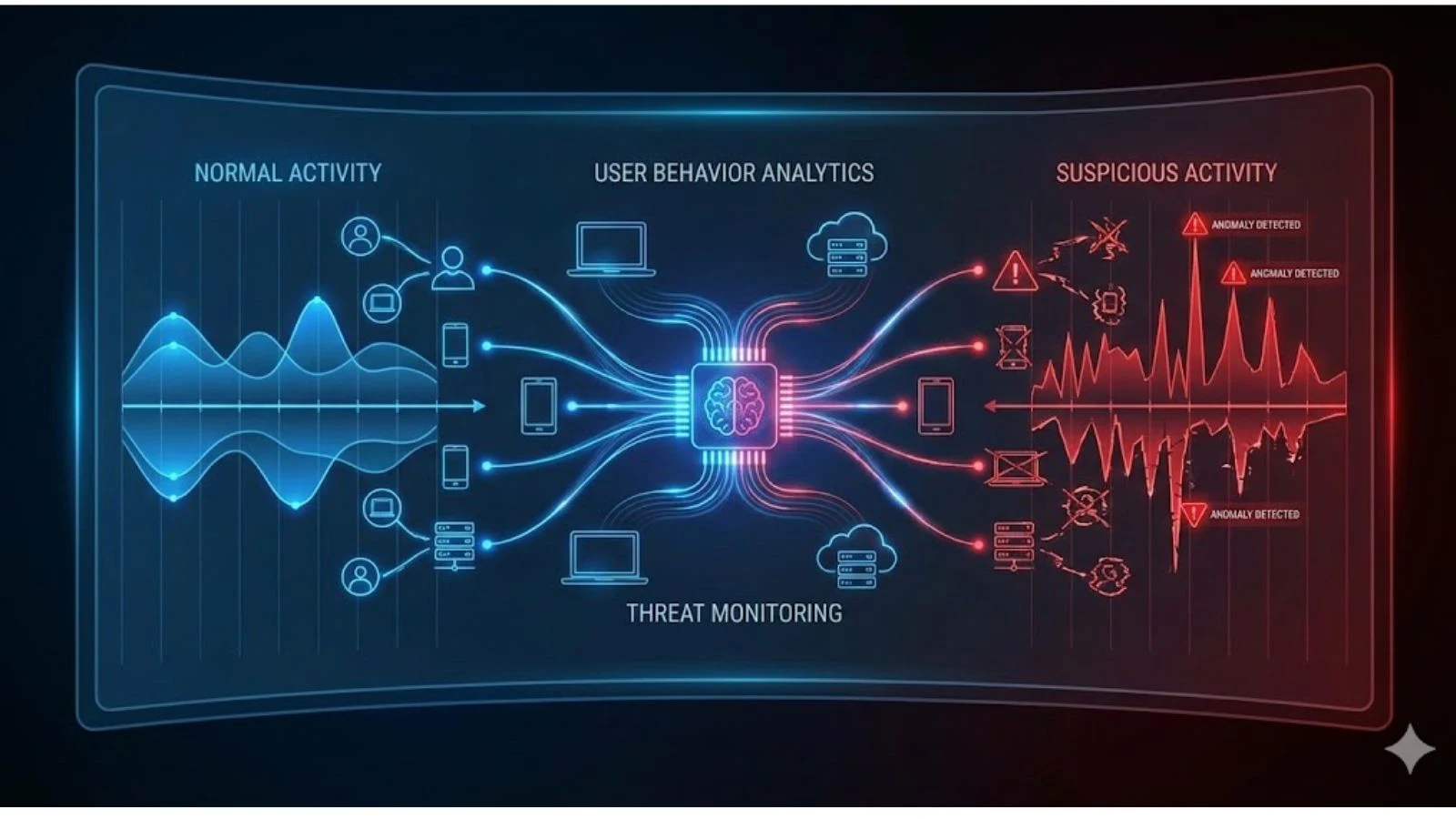
Security leaders are under more pressure than ever.
Data breaches are getting more sophisticated. Insider risks are rising. Compliance regulations are tightening. And hybrid work environments have expanded the attack surface beyond traditional office walls.
In this environment, visibility is everything.
That’s where user activity monitoring becomes essential. It gives CISOs and security teams a clear, structured view of how employees, contractors, and third-party users interact with company systems and data.
Without it, you’re operating in the dark.
With it, you gain:
- Clear audit trails
- Behavioural insights
- Faster incident response
- Stronger compliance posture
But here’s the key: user activity monitoring isn’t just about watching screens. It’s about understanding behaviour patterns, identifying anomalies, and reducing risk before it escalates.
Modern organizations use user activity monitoring software to collect and analyse activity data across devices, applications, and networks. When combined with real time user monitoring capabilities, it transforms passive logging into proactive threat detection.
You can listen to this blog here.
What Is User Activity Monitoring? 
At its core, user activity monitoring is the process of tracking and analysing how users interact with organizational systems, applications, and data.
But that definition barely scratches the surface.
For a CISO, user activity monitoring is about answering critical questions:
- Who accessed sensitive data?
- What actions did they take?
- When did it happen?
- From which device or location?
- Was the behaviour normal or suspicious?
It moves security from assumptions to evidence.
More Than Just Logs
Traditional logging captures events. But modern User behaviour monitoring software goes further by:
- Recording user sessions
- Tracking file movements
- Monitoring application usage
- Detecting policy violations
- Flagging behavioural anomalies
Instead of isolated events, you get context.
For example:
An employee logs in at 9 AM normally.
They download 5GB of sensitive files at 2 AM from a personal device not normal.
Without structured user activity monitoring, that red flag could easily go unnoticed.
How It Differs From Basic Monitoring
Many organizations confuse UAM with:
- IT system monitoring
- Network traffic analysis
- Time tracking tools
Those serve different purposes.
User activity monitoring focuses specifically on human behaviour inside digital systems. It bridges the gap between cybersecurity tools and workforce oversight by providing visibility into individual-level actions.
When combined with real time user monitoring, it enables immediate alerting for:
- Unusual login attempts
- Mass file downloads
- Privilege escalation
- Unauthorized application usage
For CISOs, this capability transforms reactive investigations into proactive prevention.
Why It Matters in Hybrid Work Environments
Remote and hybrid work models have dissolved traditional network boundaries. Employees access systems from:
- Home networks
- Public Wi-Fi
- Personal devices
- Cloud applications
This expanded attack surface increases insider risk, both accidental and intentional.
User activity monitoring provides a centralized layer of visibility across distributed environments. It ensures that no matter where work happens, actions remain traceable.
And for modern security leaders, traceability equals control.
Why CISOs Are Prioritizing UAM in 2026
Security leaders today face a more complex risk landscape than ever. Hybrid work, stricter regulations, and rising insider threats have pushed user activity monitoring to the top of the CISO agenda.
Insider Threats Are Subtle
Unlike external attacks, insider risks often look like normal behaviour. A user accessing files or downloading data may not seem suspicious at first. User activity tracking helps detect unusual patterns like abnormal download volumes or odd login times before damage occurs.
Compliance Requires Proof
Regulators want evidence, not policies. Security teams must show who accessed sensitive data and when. User behaviour monitoring software simplifies this by maintaining detailed, searchable records for audits and investigations.
Remote Work Increased Exposure
Employees now access systems from multiple devices and locations. Real time user monitoring enables faster detection of suspicious logins, unauthorized access, or unusual activity, reducing response time and impact.
Executive-Level Accountability
Boards expect measurable security metrics. With User activity tracking, CISOs can present clear reports on insider risk, privileged access, and policy enforcement.
Key Capabilities CISOs Should Look For
Not all tools are equal. Effective User activity tracking Software should provide:
- Centralized visibility across on cloud systems
- Real-time alerting
- Role-based access controls
- Tamper-proof logging
- Scalable data retention
- Detailed reporting
For organizations handling sensitive intellectual property or regulated data, advanced session recording and anomaly detection add a layer of protection.
Legal, Ethical, and Compliance Considerations
While user activity monitoring strengthens security, it must be implemented responsibly. For CISOs, balancing visibility with privacy is just as important as preventing threats.
Monitoring without governance can create legal risk, employee distrust, and reputational damage.
Here’s what security leaders must consider.
1. Transparency Is Non-Negotiable
Employees should never feel secretly watched.
Organizations should clearly communicate:
- What is being monitored
- Why is monitoring necessary
- How data will be used
- Who has access to it?
When User activity tracking is positioned as a security and compliance measure, not a spying tool, it builds trust rather than resistance.
Clear internal policies and employee acknowledgments are essential.
2. Align With Data Protection Laws
Different regions have strict privacy regulations governing workplace monitoring.
Depending on your jurisdiction, you may need:
- Employee consent
- Explicit data retention limits
- Defined monitoring scope
- Justification for data collection
User activity tracking software should allow configurable data controls to meet local compliance requirements.
3. Monitor Based on Risk, Not Curiosity
A common mistake is over-monitoring.
Effective security strategies focus on:
- Privileged accounts
- Sensitive data access
- High-risk departments
- Regulatory scope
Real-time user monitoring should prioritize unusual or risky behaviour rather than tracking every minor action unnecessarily.
Over-collection creates noise and legal exposure.
4. Protect the Monitoring Data Itself
Activity logs contain sensitive information. If compromised, they can reveal operational details.
Security leaders must ensure:
- Logs are encrypted
- Access is role-restricted
- Records are tamper-proof
- Retention policies are enforced
If monitoring data isn’t secure, it becomes another vulnerability.
5. Separate Productivity Management From Security Oversight
Although UAM can provide performance insights, security and HR objectives should remain clearly defined.
When organizations use User activity tracking primarily for compliance and insider threat detection, they maintain a stronger ethical positioning.
How to Choose the Right UAM Solution (Checklist for CISOs)
Selecting the right user activity monitoring solution isn’t about features alone; it’s about aligning with your risk strategy.
Here’s a simplified decision checklist:
1. Clarify Your Objective
Are you focused on insider threats, compliance, privileged users, or remote workforce oversight? Your primary goal should guide your tool selection.
2. Demand Real-Time Visibility
Strong solutions support real time user monitoring, enabling instant alerts and faster incident response.
3. Ensure Tamper-Proof Logs
Monitoring data must be encrypted, access-controlled, and immutable to remain audit-ready.
4. Check Scalability
Your system should support hybrid environments, growing teams, and long-term data storage without performance loss.
5. Prioritize Reporting
Look for searchable logs, compliance-ready reports, and easy export features.
6. Confirm Integration
The platform should integrate smoothly with SIEM, IAM, DLP, and endpoint security tools.
The right User activity tracking software doesn’t just collect data; it strengthens your entire security posture.
How EmpMonitor Supports Modern UAM Strategies
For CISOs looking to operationalize user behavior monitoring without adding unnecessary complexity, EmpMonitor offers a structured and scalable approach.
Instead of fragmented tracking tools, EmpMonitor centralizes visibility across endpoints, applications, and remote environments.
Key Capabilities
- Detailed user activity tracking across devices
- Real-time alerts for suspicious behaviour
- Role-based access control
- Secure, tamper-resistant logs
- Productivity and application usage insights
- Exportable compliance-ready reports
With built-in real-time user monitoring, security teams can identify anomalies instantly, whether it’s unusual login timing, excessive file downloads, or unauthorized access attempts.
EmpMonitor also supports workforce analytics, giving leadership actionable data without compromising governance standards.
For organizations balancing compliance, insider threat detection, and operational efficiency, EmpMonitor transforms user activity tracking software into a practical risk management asset.
Also Read,
What Employee Performance Metrics Should IT Managers Focus On?
Using Activity Logs To Build Productive Work Habits In Modern Organizations
Conclusion
Security leadership today demands more than perimeter defence. It requires visibility into human behaviour inside digital systems.
That’s where user activity monitoring becomes indispensable.
From insider threat detection to compliance reporting, it provides the evidence and intelligence CISOs need to make informed decisions. When implemented responsibly, it strengthens accountability without sacrificing trust.
In hybrid and cloud-first environments, the ability to observe, analyse, and respond to user behaviour in real time is no longer optional; it’s foundational.
User behaviour monitoring shifts security from reactive investigation to proactive risk control.
And for modern enterprises, that shift defines resilience.
FAQs
1. What is user behaviour monitoring used for?
It is used to track and analyse how users interact with systems, applications, and data to prevent insider threats, ensure compliance, and improve visibility.
2. Is user activity monitoring legal?
Yes, when implemented transparently and aligned with local data protection laws. Organizations should clearly communicate policies and obtain necessary consent.
3. How is UAM different from basic logging?
Basic logging records events. User behaviour monitoring provides deeper behavioural analysis, session visibility, and real-time alerting.