Since the beginning, cyber threats and insider attacks have been the most concerning subjects for businesses and organizations. Because breaching of the most classified and vital data or information perpetually can slaughter their whole existence.
No wonder the concern spiked up when the news came that Google got whacked. However, Google recently clarified that the breakdown was due to a critical system running out of storage. Numerous users are still in a state of terror regarding their data. Cyber attacks and breaches are constantly a predominant factor for cybersecurity. Do you remember that in 2012, NASA got hacked! Yes, you heard it right.
In 2012, NASA published a statement stating that it got hacked and hackers broke into its system 13 times last year, including all the employee credentials and gaining access to mission-critical projects in breaches that could comprise US national security.
Since then, The National Aeronautics and Space Administration spends only $58 million of its $1.5 billion annual IT budget on cybersecurity. And don’t forget Google’s perpetual algorithm updates, billions and trillions of scans, concealment cybersecurity, and many are under the mystery box. I guess the epicenter is transparent.
Hypothetically if NASA can get hacked, calculate the probability of your business or organization getting a cyber attack. No! We don’t want that, but it is high. ( Although I m weak in mathematics )
Impact of Cyber Threats For Small Businesses
Due to less advanced technological defenses, less awareness, and fewer resources, it is easy to target hundreds of businesses and eventually thousands. It proffers small businesses as an easy target for hackers than magnanimous organizations.
According to some statements, less than 500 employees carry the loss of an aggregate of $3.5 million per attack. This amount of money can be overwhelming for small businesses.
Whether it’s a meager or well-reputed business, all are excellent dummies for cyberattacks, and inadequate consideration can cause loss. The expense of cybersecurity in 2016 was $3 trillion, and at the end of 2025, specialists prophesied that cybersecurity spend could relinquish $10.5 trillion every year.
Phishing Cyber Threats Attack
One of the challenging and occurring warnings for every type of business is phishing attacks. Technically, it happens when the cyber attacker pretends to trust the individuals who manipulate the user to either click or download wicked data or grant access to delicate info, account aspects, or credentials. This sort of cyberattack is email-borne that includes the email receivers revealing the malware via the hyperlink in the message.
Malware Cyber Attack
On the list of cybersecurity threats, malware attacks are one the second place. Consist damaging cyber threats such as trojans and viruses. It does have the power to cripple the system or device, which later demands expensive repair expenses. Usually, they grow from malicious website downloads, spam emails, or become poisoned by the machines or devices.
Ransomware cyber threats
One of the most common and lucrative forms of cyber attack poisoned millions of businesses every year. Foremost it infects the company’s data for access and then manipulates the victim to pay the ransom to unlock the data.
It grants the companies two choices; either satisfy the ransom with a sum of money or let the system cripple.
All the top most dangerous kinds of cyber threats are damaging, and some events irrevocable. Have you heard the saying, prevention is better than cure, YES!, right? So what would prevent cyber attacks and threats without expending half of the business budget on the security implementation?
EmpMonitor – A Cloud Based Cyber
Security Solution
EmpMonitor is cloud-based monitoring software that manages all the computers in your organization remotely from a centralized location. Real-time monitoring, automatic screenshots at regular intervals, and automatically save data in the cloud.
To enshield from the insider threats, EmpMonitor does have the reinforce features like ;
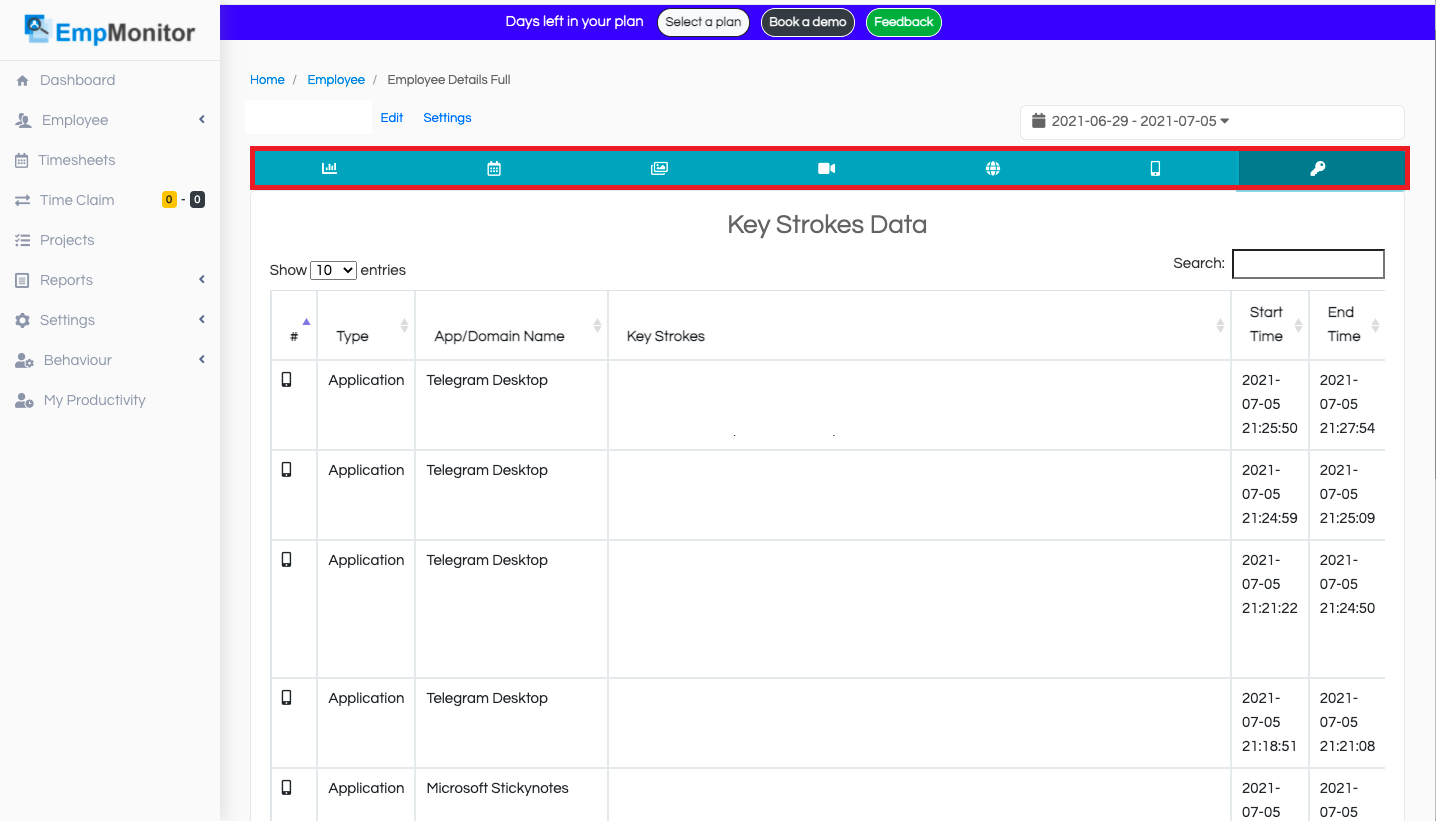
Keystroke –
Monitor what the user is typing and keep the record of the employee typed on which program or window. Recollect the data up to around 180 days with individual specified data for better analysis and tracking. Every deleted and typed key on each application and website with time and date record keeping.
Stealth Mode-
It is completely invisible unless you make it visible. Neither appears in the program list or task manager.
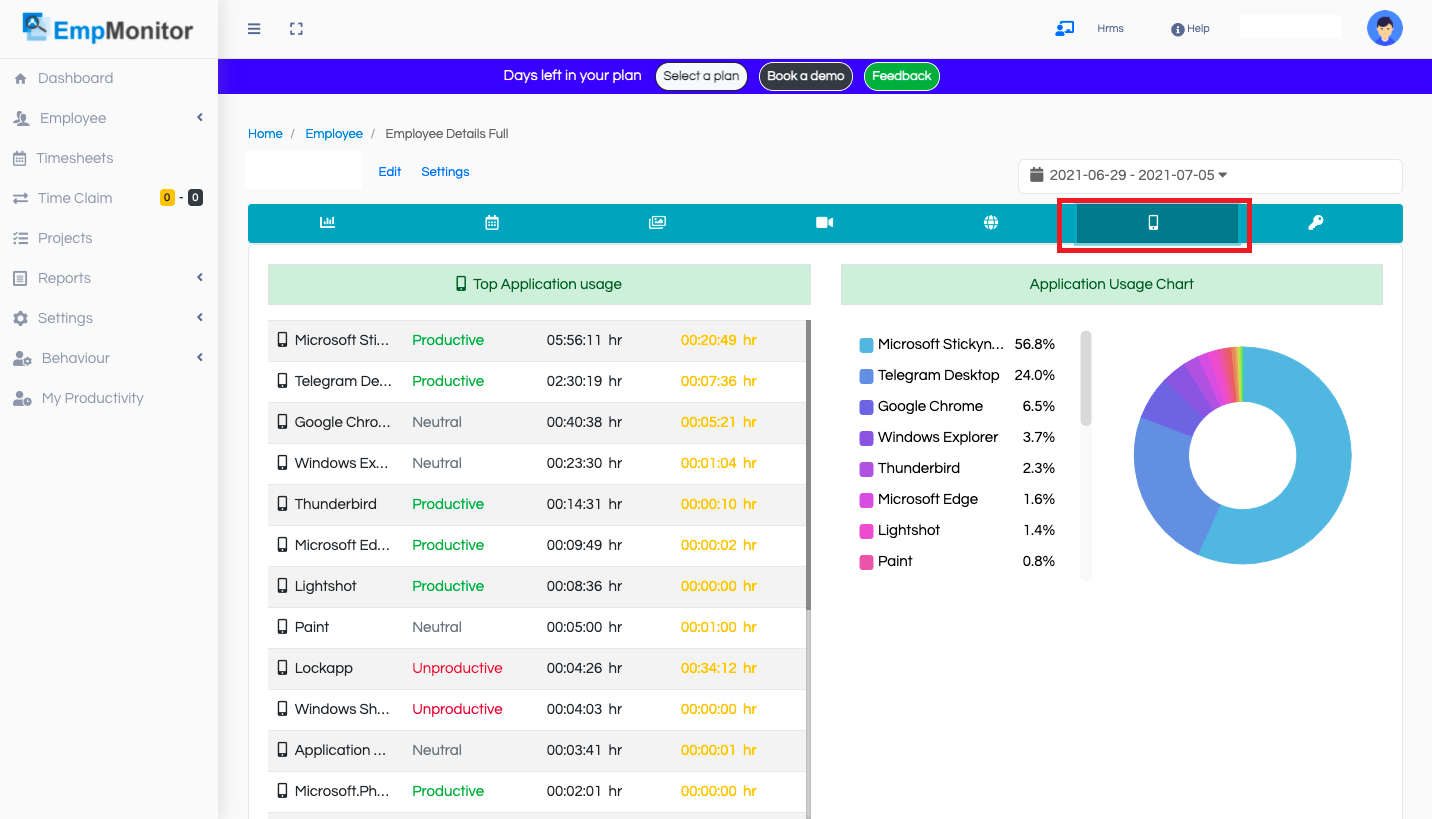
Application and website History-
Track each URL visited by the user and the time spent at a single website. In one glance, look up the top 10 websites used in real-time and view the history up to 180 days.
EmpMonitor is power-packed with multiple features both advantageous for businesses and management with a breeze in the budget. Cut the cords of cyber threats or attacks and alert the nerve before it turns into a dangerous threat. try EmpMonitor today!
Cyber security becomes more evident, and the root of concerns and discussions in every organization and business after the pandemic hits the world when all the companies have to wrap up the work to remote working culture. It makes the business world more vulnerable to cybercrime attacks. So what can be the precautionary steps taken by every organization to decline the graph of these attacks?
How to Protect Your Business From Cyber Threats?
Protecting the business and organization from dangerous cyber attacks is taking necessary precautions and investing in the best data loss prevention software and others outlined to warn the threat and keep an eye on the suspicious activities. Like EmpMonitor, intelligence meant to track and monitor every online and offline activity, warning of insider threats and any suspicious activity from any end.
However, there are proven tactics and precautionary steps for shielding the business from any genus of security threat like;
Instruct the Working Professionals For Cyber Attacks
Working professionals should have comprehensible knowledge of cybersecurity threats. Businesses or organizations should spread awareness of the jeopardies and licensed measures to confront any of the disturbances.
? Employees should be conscious of the cybersecurity outlines and supplement their endeavors to intensify them.
? Address the latest and current suspicious movements or warnings in their operating system or software. Immediately, reporting the cyber attack alert the higher authorities to find the nerve of the attack.
? Create strong passwords, especially work from home, avoid messing the company’s id with the personal stuff, exclude the risk of unauthorized access to any company’s data and systems.
Invest in Security Software
As mentioned earlier, investing in cybersecurity software can heighten functionalities and eliminate the extra burden of tasks and monitoring. Also, evaluate the cyber health of the organization every once in a while.
Data Encryptions
One of the vital elements of protecting the business from any data breaching and cyber attack, encrypting the data, executes the task challenging for the hackers to damage or temper the data. Install the proxy to encrypt the data.
Follow the Online User Behavior
Tracking the online activities ensures the employees or users are following the protocols of cybersecurity. Bringing your device is also one of the cybersecurity threats to counter this scan of any hard drive or USB drive before allowing it to be used.
Cyber Insurance
Protect business assets by implementing cyber insurance because it doesn’t matter whether the attack will happen or not. Taking precautionary steps for preventing it is mandatory for the business. Cyber insurance allows to tackle any outbreaks and restrain the coverage of business continuation. Make it accessible and affordable for every type of business.
Watch How To Manage Employee’s Workplace Behavior Analytics?
Read Our Latest Blogs;
Access Management: Why Is It So Important | 09 Benefits Of IAM
Is managing remote employees more difficult than ever in this WFH culture?
Brushing Off!
The phenomenon of remote working creates the vulnerability of getting cyber attacks and momentous cyber threats of phishing, insider threats, SQL injections restrain the consequences era. However, the best way to protect the business from these hazardous incidents is to rely on cybersecurity software and DLP software alerts before the damage turns into an irreversible loss.
What are your thoughts about cyber threats or security? Quote in the comment section below.
Are you still lacking behind or suffering from continuous cyber threats? Get the right solution for your businesses in budget-friendly plans. Try EmpMonitor today!