When it comes to information security, the ISO 27001 standard is known to be one of the most secure methods for the protection of sensitive information. However, obtaining ISO 27001 certification is not just about implementing the latest technology and securing computer systems; it is also about taking a holistic approach that involves the human factor.
The human factor is often the weakest link in the chain of security, and training employees on good security practices is essential.
You can listen to this blog here.
ISO 27001 And Its Importance
ISO 27001 is an international standard that provides criteria for the establishment, implementation, operation, monitoring, review, maintenance, and improvement of an information security management system (ISMS). The purpose of 27001 certification is to assist organizations in safeguarding their sensitive information by managing risks effectively.
A good ISMS not only deals with technical issues such as network security and encryption but also with operational and human factors, such as employee behaviour and awareness. It is necessary to develop a security culture where all members of an organization are aware of their responsibility for protecting information.
The Human Element in ISO 27001 Certification
While 27001 focuses heavily on systems and processes, it cannot succeed without the commitment and involvement of employees. The human element plays a critical role in ensuring the success of an ISMS. Employees must understand security policies, be trained on security best practices, and be motivated to adhere to these guidelines consistently.
Training programs that cover topics like data protection, phishing prevention, and secure password practices are essential. Regular awareness campaigns and updates on potential threats, such as social engineering attacks, help keep security at the forefront of employees’ minds. Furthermore, organizations must establish clear protocols for employees to follow in case of security incidents, ensuring a swift and effective response.
Building a Security-Focused Culture
To meet ISO 27001 standards, an organization must build a security-focused culture where employees feel responsible for information security. This involves making security a priority in daily operations, not just a task delegated to the IT team.
One of the key principles of the 27001 information security management system is continuous improvement. This doesn’t just apply to systems and technologies; it also extends to how employees interact with security practices. Regular security audits, feedback sessions, and refresher training courses are essential for keeping security top-of-mind.
EmpMonitor: Supporting ISO 27001 Compliance
Achieving and maintaining ISO 27001 certification is an ongoing effort that requires constant monitoring, evaluation, and improvement.
EmpMonitor is a powerful tool that can help organizations in this regard by providing real-time monitoring of employee activities.
By ensuring that employees are adhering to security protocols and best practices, EmpMonitor plays a critical role in maintaining a secure work environment.
With features like –
- Screen Monitoring
- Keystroke Tracking
- Productivity Analysis,
EmpMonitor allows organizations to detect potential security threats and human errors quickly. It also helps organizations ensure that employees are following internal security policies and maintaining compliance with 27001 standards.
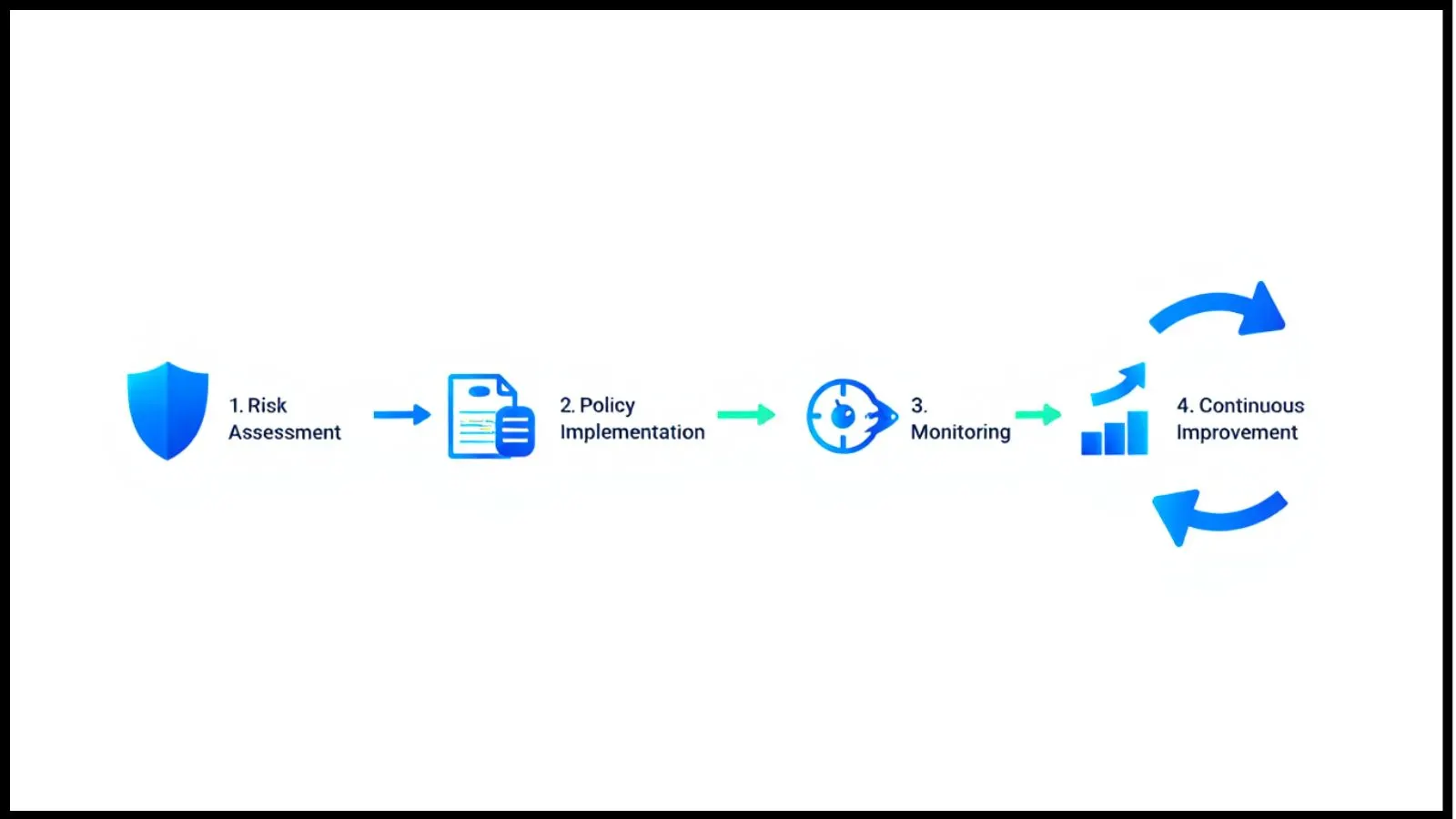
ISO 27001 Certification: What Does It Involve?
Achieving ISO 27001 certification is a multi-step process that requires thorough planning, implementation, and ongoing maintenance. The process generally involves the following stages:
- Risk Assessment: Identifying potential risks to sensitive data and determining appropriate measures to mitigate these risks.
- Policy Development: Developing comprehensive security policies that outline how information should be handled, accessed, and protected.
- Employee Training: Ensuring all employees are properly trained on security policies and understand their roles in safeguarding information.
- Implementing Controls: Putting technical and administrative controls in place to prevent data breaches and other security incidents.
- Monitoring and Auditing: Continuously monitoring the effectiveness of security controls and performing regular audits to ensure compliance.
Human Error and Its Impact on Information Security
Despite the best technologies and systems in place, human error remains one of the leading causes of security breaches. Employees may accidentally send sensitive information to the wrong recipient, fall victim to phishing scams, or ignore security protocols in a rush to meet deadlines.
To mitigate human error, organizations need to adopt proactive measures such as security awareness programs, regular audits, and tools like EmpMonitor that track employee activities and provide insights into potential security risks. By monitoring and addressing risky behaviors, businesses can reduce the chances of security incidents caused by human error.
Continuous Improvement: Ensuring Long-Term Security
27001 is not a one-time certification process; it requires continuous effort to ensure that the information security management system remains effective as the business evolves. This ongoing commitment includes regular audits, updates to security policies, and employee refresher training.
EmpMonitor can help organizations ensure continuous improvement by offering real-time insights into employee activities. By tracking adherence to security protocols and identifying areas of concern, EmpMonitor provides valuable data that can guide security enhancements and ensure that 27001 standards are continuously met.
The Role of Leadership in ISO 27001 Certification
Leadership plays a pivotal role in the success of an 27001 certification. Management must set the tone for the organization by committing to information security and ensuring that security policies are implemented effectively. Leaders should actively engage in security training, provide necessary resources, and demonstrate a commitment to ongoing improvement.
By promoting a culture of security at all levels, from executives to employees, leadership ensures that security becomes an integral part of the company’s operations, rather than just an afterthought.
Also read,
Conclusion
Achieving ISO 27001 certification is a significant accomplishment that demonstrates an organization’s commitment to securing sensitive information. However, the true success of this certification lies in integrating the human element into the information security management system. Employees must be educated, aware, and engaged in the organization’s security efforts, and leadership must provide the necessary resources and guidance to support this.
By leveraging tools like EmpMonitor, organizations can monitor compliance, track employee behaviour, and ensure that security policies are being followed. This proactive approach not only helps organizations maintain ISO 27001 certification but also creates a secure environment where information remains protected from both internal and external threats.
FAQ’s
1. How does ISO 27001 help with information security?
27001 helps organizations safeguard sensitive data by providing a systematic approach to information security. It outlines the requirements for risk assessment, data protection policies, and controls to mitigate security threats. By implementing 27001, organizations can ensure that they are actively managing and reducing risks associated with data security, ensuring the confidentiality, integrity, and availability of critical information.
2. What are the key components of an Information Security Management System (ISMS)?
An ISMS under 27001 consists of several key components:
- Risk Assessment and Treatment: Identifying risks to information security and implementing measures to manage or mitigate those risks.
- Security Policies: Establishing rules and guidelines for handling sensitive information.
- Employee Training and Awareness: Ensuring that all staff understand their roles in maintaining information security.
- Monitoring and Auditing: Continuously monitoring systems and processes to ensure security measures are effective.
- Continuous Improvement: Regularly reviewing and improving the ISMS to adapt to emerging threats and business needs.
3. How does EmpMonitor support ISO 27001 certification?
EmpMonitor can play a crucial role in helping organizations maintain 27001 certification by offering tools for real-time monitoring of employee activities. With features such as screen monitoring, keystroke tracking, and productivity analysis, EmpMonitor ensures that employees are adhering to internal security policies and best practices. By providing insights into potential security risks and monitoring compliance, EmpMonitor helps organizations remain aligned with 27001 standards.