Think your employees’ credentials are safe? Unfortunately, that’s not always the case. Even a single leaked password can put your entire organization at risk. This is where dark web monitoring comes in.
Dark web surveillance involves scanning hidden online marketplaces, forums, and paste sites to detect stolen credentials, sensitive data, and leaked company information. By identifying compromised credentials early, businesses can act before hackers exploit them.
Organizations are increasingly relying on dark web monitoring services to protect their workforce, secure sensitive systems, and maintain compliance with regulations. In this guide, we’ll explore how employee credentials end up on the dark web and the risks involved.
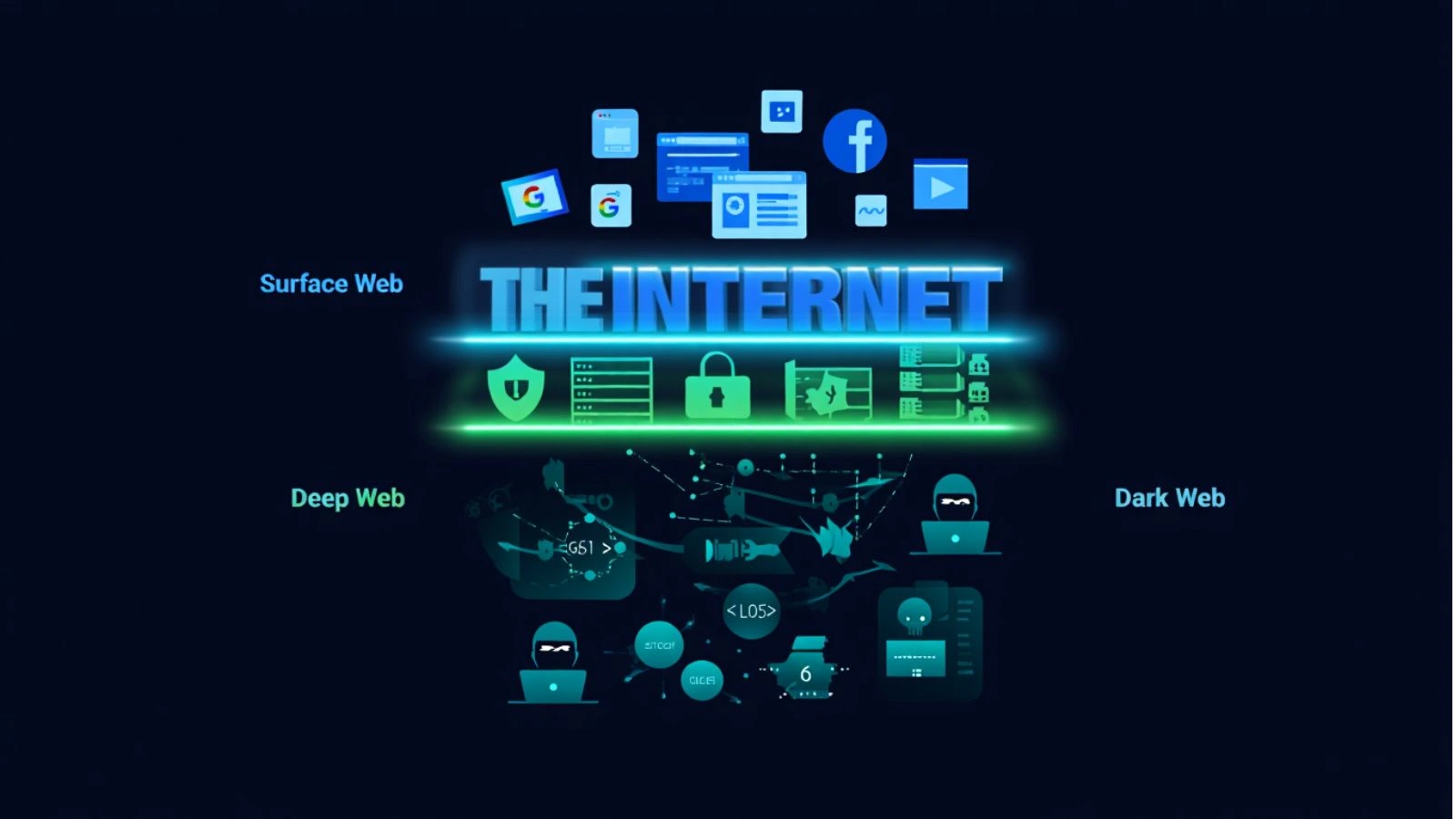
What Is the Dark Web?
The internet isn’t just what you see on Google. It has multiple layers:
- Surface Web: Websites indexed by search engines, like news sites or online stores.
- Deep Web: Password-protected pages, private databases, and internal company systems.
- Dark Web: Hidden networks accessible only via special browsers, often used for anonymity.
The dark web is notorious for hosting stolen data, including login credentials, financial information, and personal details. Employees’ usernames, emails, and passwords can appear here after data breaches or phishing attacks.
Even if your IT systems are secure, compromised employee credentials can provide hackers with access to sensitive company data. That’s why dark web monitoring for business is essential; it’s about seeing threats before they become breaches.
How Credentials End Up on the Dark Web?
Employee credentials can appear on the dark web in several ways:
- Data Breaches: Hackers target companies and online services to steal user information, which is later sold or shared on the dark web.
- Phishing Attacks: Employees may unknowingly enter passwords into fake websites, giving attackers access to corporate accounts.
- Weak or Reused Passwords: Using simple or repeated passwords across multiple platforms increases the likelihood of exposure.
- Insider Leaks or Accidental Exposure: Sometimes, employees inadvertently share sensitive data through unsecured channels.
Once credentials are compromised, attackers can attempt to access corporate systems, internal databases, or cloud accounts. For remote and hybrid teams, where employees use multiple devices and networks, the risk grows even higher.
Risks of Compromised Employee Credentials
When employee credentials are exposed on the dark web, the consequences can be severe:
- Unauthorized Access: Hackers can infiltrate corporate systems, emails, and cloud platforms.
- Financial Loss and Fraud: Compromised accounts can lead to stolen funds, fraudulent transactions, or ransom attacks.
- Reputation Damage: A breach can erode client trust and harm your company’s brand.
- Regulatory Compliance Violations: Exposure of sensitive data may result in fines under GDPR, HIPAA, or other regulations.
- Increased Risk for Remote Teams: Employees working from home may inadvertently introduce vulnerabilities if devices or networks are compromised.
Understanding these risks highlights why proactive dark web surveillance is crucial for businesses of all sizes.
How Dark Web Monitoring Works?
Dark web surveillance involves scanning hidden online spaces for stolen credentials and other sensitive company data. Here’s how it typically works:
- Continuous Scanning: Tools scan marketplaces, forums, paste sites, and other dark web sources for leaked usernames, passwords, and email addresses.
- Alerting Security Teams: When employee credentials or company data are found, IT teams receive immediate notifications.
- Integration with Security Systems: Monitoring tools often integrate with existing IT infrastructure to streamline threat response.
- Risk Assessment: Alerts may include the severity of exposure, helping prioritize actions.
For organizations using Google Workspace or other platforms, specialized dark web monitoring for business tools can identify unauthorized third-party access, ensuring IT teams are always aware of potential threats.
Also Read:
How Can You Start Securing Remote Workers?
How Is Radical Transparency Reshaping Data Security And Trust?
Benefits of Dark Web Monitoring Services
Implementing a dark web surveillance solution offers several advantages for businesses:
- Early Detection of Compromised Credentials: Find exposed employee accounts before hackers exploit them.
- Reduced Risk of Breaches: Identify vulnerabilities proactively and prevent unauthorized access.
- Regulatory Compliance Support: Helps meet requirements under GDPR, HIPAA, and other data protection laws.
- Protection for Employees and Company Data: Ensures personal and corporate information stays secure.
- Enhanced Response Capabilities: Security teams can act quickly with alerts and actionable reports.
By monitoring potential threats, organizations can safeguard sensitive data while maintaining smooth business operations.
How EmpMonitor Supports Credential Security?
EmpMonitor goes beyond traditional monitoring by helping organizations protect employee credentials and sensitive data in real time. It allows the management to block such sites which may seem to compromise the security for remote and hybrid teams.
Employee Activity Tracking
Monitors app and website usage to identify potential risky behavior that could lead to credential exposure.
Alerts and Reports
Generates actionable insights on account usage, password hygiene, and suspicious activity, helping IT teams respond quickly.
Remote Workforce Coverage
Tracks activity across devices and locations, ensuring visibility even when employees work from home or other remote locations.
Integration with Security Tools
EmpMonitor complements web monitoring and also allows blocking dark websites providing an internal oversight, making it easier to detect, respond to, and prevent breaches.
With EmpMonitor, companies gain proactive visibility into potential risks, protecting both employees and corporate systems before credentials are exploited.
Best Practices for Protecting Employee Credentials
Responding to Compromised Credentials
Even with monitoring, credentials can still be exposed. A clear response plan is essential:
- Immediate Password Reset: Change affected passwords across all systems.
- Notify IT and Security Teams: Ensure proper tracking and investigation.
- Enable MFA: If not already in place, activate multi-factor authentication for affected accounts.
- Review Access Logs: Check for unusual login attempts or unauthorized access.
- Employee Awareness: Inform the employee and guide safe practices.
Having a defined response process reduces the impact of breaches and strengthens overall security.
Future Trends in Credential Security and Dark Web Monitoring
The security landscape continues to evolve, and so do monitoring strategies:
- AI and Machine Learning: Automated detection of suspicious activity and credential exposure.
- Behavioral Biometrics: Combining typing patterns, login behavior, and device fingerprints to verify identity.
- Integration Across Platforms: More comprehensive monitoring spanning cloud, email, and collaboration tools.
- Proactive Threat Intelligence: Continuous updates on new dark web marketplaces and threat actors.
- Enhanced Employee Training: Using real-world examples from monitoring alerts to educate staff.
Staying ahead of these trends ensures organizations can protect employee credentials proactively and reduce risks before breaches occur.
Conclusion
Employee credentials are a prime target for cybercriminals, and the dark web makes it easier for stolen information to circulate unnoticed. By implementing dark web surveillance and proactive security measures, businesses can detect compromised accounts before attackers exploit them.
Tools like EmpMonitor complement these efforts by tracking employee activity, monitoring password hygiene, and alerting IT teams to suspicious behavior, all while supporting remote and hybrid work environments.
By combining monitoring, employee education, and strong password policies, organizations can protect both their workforce and sensitive corporate data. Staying vigilant ensures that your company is prepared to respond quickly to threats, maintain compliance, and minimize risk.
FAQ’s
1. How do dark web monitoring services work?
These services continuously search marketplaces, forums, and paste sites for compromised accounts, then alert security teams with actionable reports.
2. Why are employee credentials often exposed?
Credentials can be leaked through data breaches, phishing attacks, weak or reused passwords, or accidental insider disclosures.
3. Can remote companies protect credentials effectively?
Yes. By combining dark web monitoring, secure password practices, MFA, and tools like EmpMonitor, organizations can maintain visibility and protect credentials across distributed teams.