With the vast interconnected technologies and seamless information exchange, the potential cases of internal threats have become quite a concern for organizations. That’s why it becomes essential for them to utilize insider threat detection so they can identify and prevent such risks from happening.
According to a report, the new employees in any corporation currently were the primary cause of security incidents. Even if you do your best to safeguard your data against IT security threats like malware and ransomware, you must not forget that probably, within your own organization, there could be some insiders with ill intent.
So, you must know how to identify such insiders and mitigate them from your organization. The process to do so is called insider threat detection.
There are various ways to pinpoint the insider threats. So, in this blog, we are going to discover some of them. And provide you with secure solutions to prevent security threats in your firm.
In a hurry? Listen to the blog instead!
What is an Insider Threat?
An insider threat refers to the risk posed to an organization’s security and data integrity by individuals within the organization itself, such as employees, contractors, or business associates. These people can misuse their access privileges for malicious purposes that may harm the company.
These threats can take various forms, including unauthorized data access, theft, sabotage, or sharing sensitive information with external parties. Insider threats can be intentional or accidental and often require sophisticated monitoring and detection mechanisms to identify and prevent.
Safeguarding against insider threats is crucial in maintaining the confidentiality, integrity, and availability of an organization’s data and systems.
How To Detect Insider Threats?
Insider threat detection has become paramount in today’s digital landscape, where organizations face increasing risks from within their own system. Safeguarding sensitive data and operations requires a proactive approach.
Therefore, every organization must ensure that employees comply with specific rules and policies. And safeguard sensitive data and operations while taking a proactive approach to prevent any form of breaches in their firm.
Read More
How To Protect Your Data From Insider Threats?
The Ultimate Solution for Data Loss Prevention
Create a Bias-Free Workplace with Real Time Employee Tracking
Best Practices For Insider Threat Detection & Prevention
User Access Management:
This process involves granting individuals access to only the systems and data necessary for their roles, following the principle of least privilege.
Since properly managing user access is a foundational pillar of insider threat management and prevention, regularly review and update access permissions as employees change roles or depart from the organization.
Additionally, you can also implement Multi-factor authentication to prevent any security threats. It will help you ensure that even if creds are compromised, unauthorized access remains a significant challenge, even for insiders.
User Behavior Monitoring:
Thanks to the real-time monitoring features of workforce management systems, it has become easier for management to track any suspicious activities in their firm.
Using this feature, employers can also analyze the user behavior of their employees. So they can establish a baseline of normal activities and swiftly identify anomalies that might indicate a potential insider threat.
This proactive approach allows for the early detection of unauthorized access, data exfiltration, or unusual patterns of behavior that could signify a breach.
Also, user behavior monitoring provides a dynamic defense against insider threats, helping organizations stay one step ahead in safeguarding their sensitive data and assets.
Security Awareness Training:
Insider threat detection, in most cases, concerns tracking the malicious staff who willingly pose a threat to all, but what about accidental breaches?
You can, undoubtedly, catch them off guard as well, but the solution to accidental insider threats is not punishment but prevention. What you must strive to do is train your employees beforehand so that they don’t become a security risk later on.
Introduce various employee-friendly, easy-to-grasp IT security training. Teach your colleagues how cyber attackers target their emails and IPs, and make them understand why they must never work on public WiFi.
Educate them about the remote access risks, the dangers of firmware security, and how to identify and get rid of malware, adware, etc.
The more your staff knows about cybersecurity and data management, the more they can identify, report, and avoid any abnormal or risky behavior prevailing online or among their fellow employees.
Data Loss Prevention (DLP) Tools:
Data loss prevention tools can help you identify any potential data threats or breach issues in your organization. These tools can monitor, detect, and mitigate the unauthorized movement of sensitive data, both within and outside the network.
It can also identify suspicious or unauthorized access, usage, or transmission of confidential information. Since it offers real-time alerts and automated response mechanisms, helping security teams swiftly intervene when insider threats are detected.
DLP tools also support policy enforcement, ensuring that employees adhere to data security guidelines, and can even block or encrypt data to prevent unauthorized disclosure. Overall, DLP tools serve as a crucial barrier against insider threats, safeguarding an organization’s most valuable digital assets with precision and efficiency.
Use Monitoring Tools For Insider Threat Detection:
Nowadays, most organizations rely on monitoring tools to keep track of their employee’s work activities. However, this not only helps them monitor their work, but they can also check on suspicious activities that may indicate an insider threat.
One such tool is EmpMonitor, which is instrumental in implementing insider threat prevention strategies. EmpMonitor utilizes advanced algorithms and behavioral analytics features that trigger alert notifications on suspicious activities. Its behavior monitoring feature allows organizations to create rules and policies for their workforce.
So, whenever someone in the organization accesses any unauthorized data or may be involved in suspicious activity, it will trigger an alert notification. Thereby, you can prevent any wrongful action that may cause any threat to your firm.
EmpMonitor: The Proactive Solution for Insider Threats
EmpMonitor equips you with insider threat detection tools to monitor, restrict, and respond to insider threats in real-time. By proactively addressing potential risks, you can maintain a secure environment and protect sensitive data from internal threats. It’s a comprehensive solution designed to simplify insider threat detection and prevention, helping you safeguard your organization’s digital assets effectively.
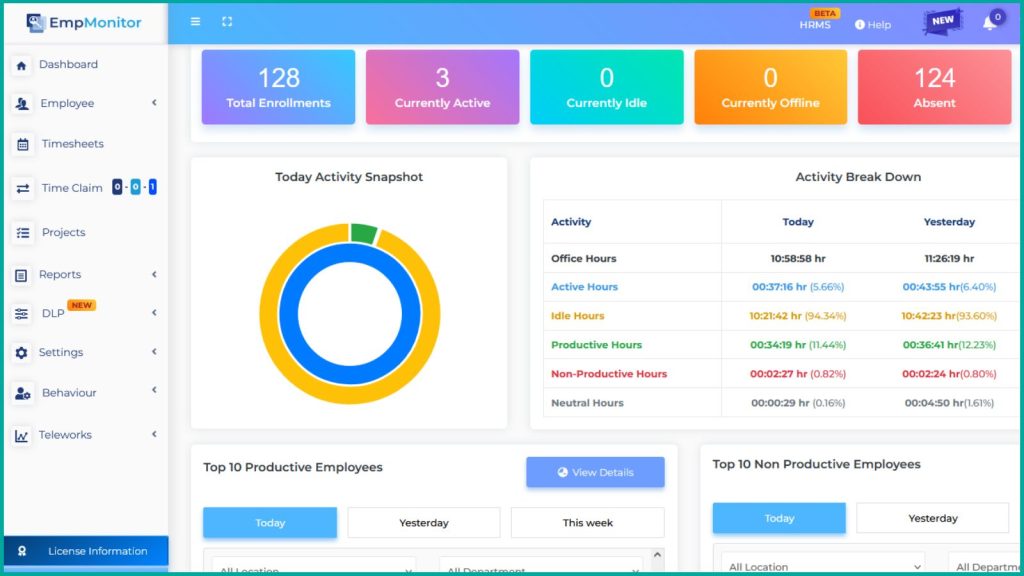
Real-Time Monitoring:
It offers comprehensive real-time monitoring capabilities, enabling you to observe your employees’ computer activities as they happen. This means you can have immediate visibility into what tasks they are performing on their computers. This feature allows you to stay informed about their digital actions, enhancing your ability to detect any unusual or potentially harmful behavior promptly.
Keystroke Logger:
With EmpMonitor’s Keylogger feature, you gain access to an invaluable tool for security. This feature records every keystroke made on monitored computers, providing you with deep insight into what is being typed. This meticulous monitoring ensures that sensitive data, passwords, and confidential information remain secure. It allows you to track every keystroke made by employees, helping to prevent data breaches or unauthorized access.
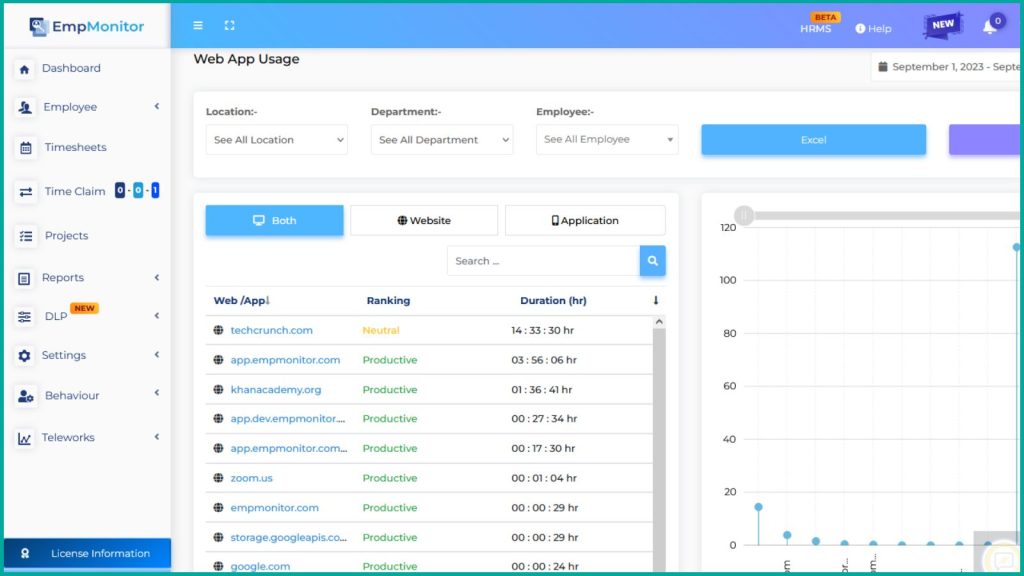
Web Application Monitoring:
EmpMonitor’s Web Application Monitoring feature empowers you to track the usage of web applications by your employees. This is particularly essential for identifying any unauthorized or risky online activities within your organization. By monitoring web application usage, you can ensure that employees adhere to company policies and avoid potentially dangerous online behavior that could compromise your network’s security.
Web and Application Blocking:
This feature provides you with the ability to control and restrict access to specific websites or applications that might pose security risks. By blocking access to these potentially harmful resources, you can maintain a secure network environment. EmpMonitor helps you enforce internet and application usage policies, reducing the likelihood of insider threats arising from the misuse of digital resources.
USB Detection:
EmpMonitor’s USB Detection feature is a vital component of insider threat prevention. It instantly alerts you to any unauthorized use of removable storage devices like USB drives. This real-time monitoring ensures that data leaks or unauthorized data transfers via USB devices are promptly identified and mitigated, adding an extra layer of security to your organization.
Behavior Monitoring:
Its Behavior Monitoring feature introduces an alert-based mechanism where you can establish rules and policies that employees must adhere to. By monitoring employees‘ digital behavior against these predefined policies, you can quickly detect any deviations or violations. This proactive approach empowers you to maintain a secure environment by identifying potential insider threats before they escalate.
If an employee doesn’t comply with organization regulations, it triggers an alert notification. So you can take preventive measures to avoid any internal breaching issues.
EmpMonitor provides a comprehensive suite of tools to enhance your organization’s insider threat detection and prevention capabilities. These features, when used effectively, enable you to maintain a proactive stance in safeguarding your company’s sensitive data and network security.
Wrapping It Up
Insider threat detection is an essential safeguard that no organization can afford to overlook, particularly in the era of remote work. Regardless of how stringent your data protection measures may be, it’s imperative to remain vigilant against potential internal risks.
Training your IT staff to effectively track and mitigate these threats is a proactive step towards bolstering your company’s security. Ensuring that your implemented policies are not just in place but actively safeguarding your business is key.
The tips we’ve outlined here serve as a solid foundation for enhancing your insider threat detection and prevention strategies while also considering potential performance management system pitfalls.
We understand that the security landscape is ever-evolving, and we’re here to assist you in elevating your company’s defenses to the next level.
Don’t hesitate to reach out to us today for expert guidance and support on your journey towards a more secure business environment.